Security BSides NoVA 2017 Retrospective
02 Mar 2017I must be doing something right because they keep sending me to security conferences.

After going to ShmooCon last month, I got the opportunity to attend the inaugural Security BSides Northern Virginia conference on February 25. As a 1 day event, it was pleasantly brief and packed a lot of talks without requiring me to commit a full weekend. Also, it took place in Herndon, which is pretty easy to get to and didn’t require a trip on the DC metro.
Like with ShmooCon, I made a list of things that stood out to me at the conference.
-
The first thing I noticed when walking in is this conference attracted a lot of big sponsors. ShmooCon actively limited the sponsorship spots and tried to showcase smaller companies, but this one had all the big names: SANS, ISC², Symantec, and pretty much ever contractor from the DC metro area.
I don’t have strong feelings about this, but I was surprised since I sort of assumed that BSides was informal and driven by community individuals (I mean, the main website is a PBworks wiki running with an educational license, so I really didn’t expect to see Fortune 500 companies setting up booths). I guess it’s cool that the BSides NoVA organizers were able to get big names for the first conference. -
Initial keynote was by Tennable co-founder Ron Gula (@rongula) under the title Cyber Security 2017: Trends and Start Ups which rolled three talks into one on the topics of 1.) the cyber security market, 2.) new rules for business and 3.) how to pitch a cyber security startup to a VC.
It was oddly refreshing to have someone talk about the intersections of startup culture and hacker culture. They both have a lot of common ground but tend to get mired by ideology.
My favorite part of his talk was his take on the traditional 5 slide pitch deck (they spend too much time on posturing and not enough on describing the problem being solved).
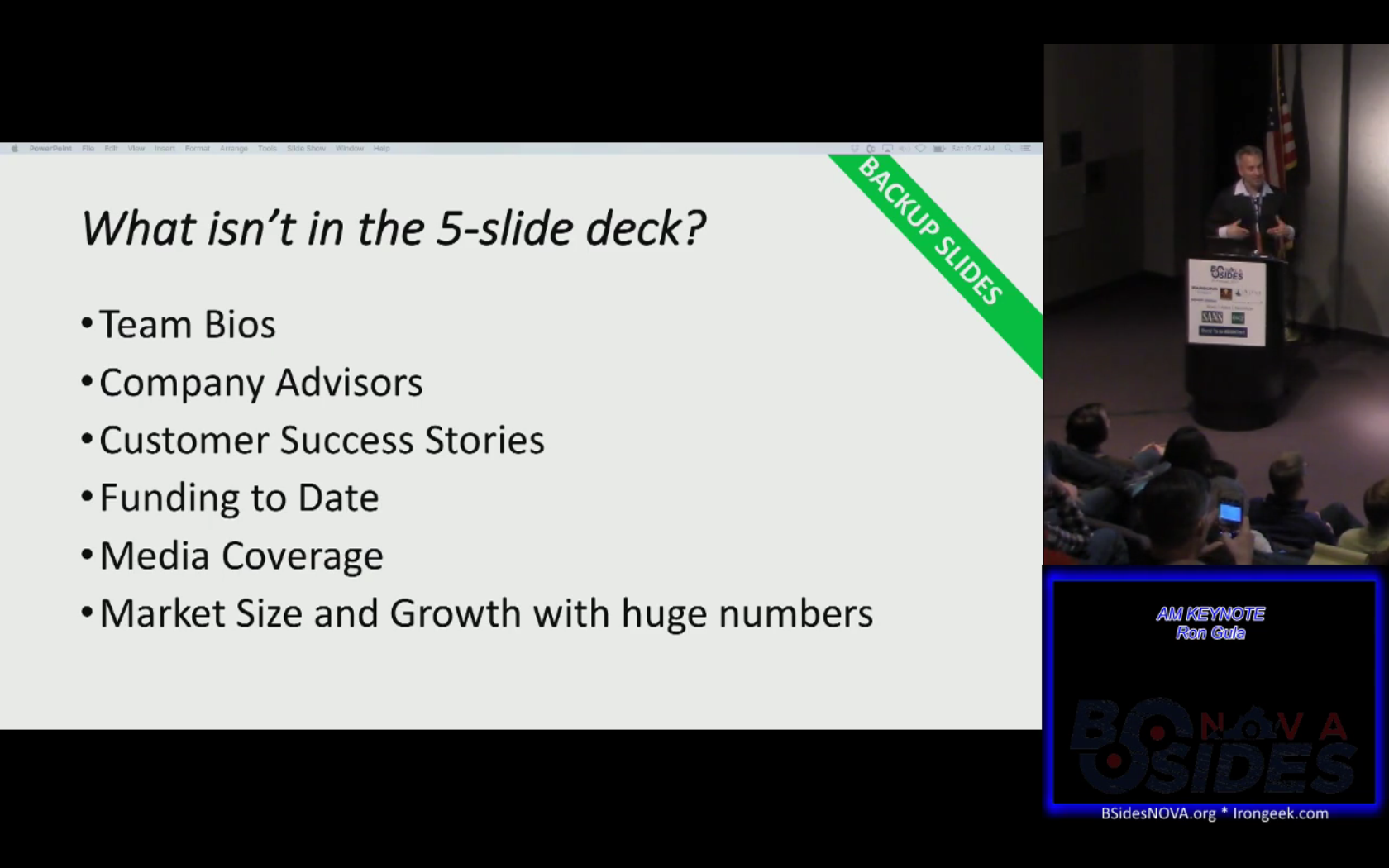
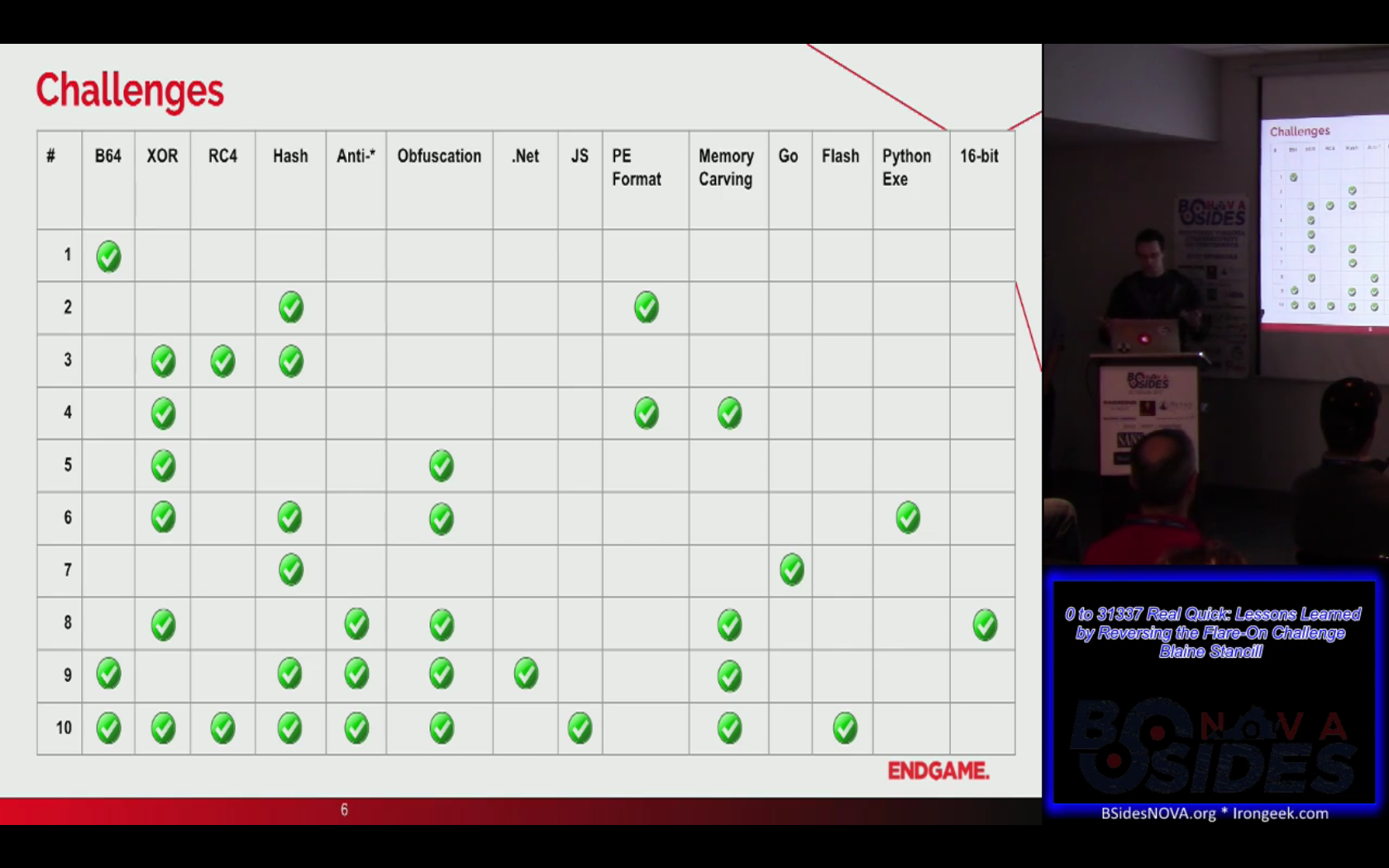
- The talk 0 to 31337 Real Quick: Lessons Learned by Reversing the Flare-On Challenge was a retrospective on last year’s FLAREOn Challenge presented by two
Endgame developers Josh Wang (@rh0gue) and Blaine Stancil (@MalwareMechanic).
These challenges were what really got me into doing reverse engineering, so I was excited to meet someone who actually completed all of them. They didn’t reveal any of the answers, but instead provided a rundown of all the techniques they saw.
This slide was the central point of the talk since it provided a table with the challenges and which reverse engineering techniques were used to solve each one:
-
Another interesting talk was Doomsday Preppers: Fortifying Your Red Team Infrastructure by Steve Borosh (@424f424f) and Jeff Dimmock (@bluscreenofjeff). It focused on how a red team can setup a successful pen test by building out simple, redundant, and redeployable networks to keep the attack alive, even if the blue team takes active steps toward blocking it.
I kind of assumed that red teams weren’t very organized and just grasped for footholds until they got the results they needed, but this really changed how I look at red team/blue team exercises. -
The final keynote was by Georgia Weidman (@georgiaweidman) whom I went to college with at James Madison University. She’s been much more successful than me since then. The organizers unfortunately put her keynote in the foyer of the building instead of an auditorium and that was a terrible idea; the sound system was awful and it was happening alongside the happy hour so it was hard to hear anything over the noise. My biggest complaint about the conference is that they messed this up so badly.
- But hey, there was free alcohol and food.
-
In addition to talks, I dropped into a few workshops. There was a Malware Analysis 101 workshop in the schedule, but there must have been some confusion when printing the schedule because it was actually an OWSAP workshop on identifying attack patterns from network packet captures.
The other workshop I did was a Forensics 101 course that was very well put together and instructed by Marcelle Lee (@marcelle_fsg), Brian Moran (@brianjmoran) and Courtney Lancaster (@allth3things).
The wifi at the conference was pretty bad; probably because it wasn’t designed to hold a ton of people all at once. I made the mistake of not downloading the workshop materials in advance. A lot of people did the same thing. To remedy this, they began passing around a thumb drive with all the materials. At a security conference. During a session on malware. Let this sink in.

-
The badges are awesome. They are an electronics reference board so they are actually pretty useful after the con.

- I saw Bruce Potter (@gdead) wandering around. It’s kind of cool to recognize people from other conferences.
Overall it was a fun conference. Most of the talks were aimed at a broader audience so it was highly accessible for all levels of experience. I definitely plan on returning.
